
- This event has passed.
ISiM Workshop on Intelligence & Security Informatics June 17-19, 2010
June 17, 2010 - June 19, 2010
Combating terrorism has occupied centre-stage across governments, security agencies, policy makers, academia, industry and society at large for obvious and understandable reasons. In the academic and industry circles, past decade has witnessed significant interest in security-related research in a wide range of applications spanning across national and international security, economic and societal security, and including personal and community security. Academic disciplines especially centered on Information Technologies such as information and computer sciences, information systems, human-computer studies, technology adoption, and policy studies have made rapid progress in developing and evaluating customized frameworks, methodologies, techniques, and systems to meet specific information processing and knowledge management challenges of “security” and “Intelligence”. An emerging field of cross-disciplinary study, called the Intelligence and Security Informatics (ISI), encompassing these efforts through an integrated technological, organizational, and policy-based approach has evolved. This multidiscipline is shaped by research and applications in fields from data/text/web mining to knowledge management to cognitive science to social psychology. The emergent field also has spawned professional societies and conferences, to build a professional community –
This emergent field has good prospects for and demands best of the young minds to expand and strengthen the domain and help contribute to the end goal of Secure and Smart society. The Workshop would help achieve this goal.
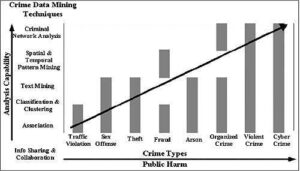
Figure 1. Research framework for ISI from H. Chen, “Intelligence and Security Informatics for International Security: Information Sharing and Data Mining,” Springer, 2006.
This workshop on ISI 2010 will provide a learning platform for students and professionals, who focus on ISI research. We believe that this summer school will enrich the understanding of the emerging domain of ISI.
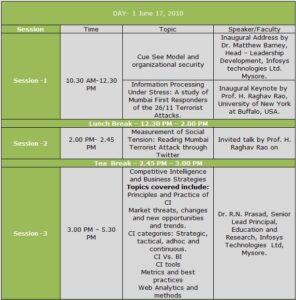
The Three day Workshop will have one talk and three Tutorials:
Talk: Competitive Intelligence and Business Strategies by Dr. R.N. Prasad, Senior Lead Principal. Education and Learning Division, Infosys Technologies, Mysore.
Topics covered include:
- Principles and Practice of CI
- Market threats, changes and new opportunities and trends.
- CI categories: Strategic, tactical, adhoc and continuous.
- CI Vs. BI
- CI tools
- Metrics and best practices
- Web Analytics and methods
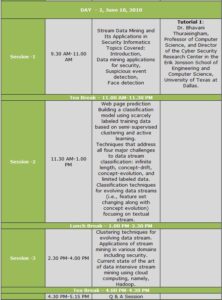
Tutorial 1: Stream Data Mining and Its Applications in security informatics by Dr. Bhavani Thuraisingham, Professor of Computer Science and Director of the Cyber Security Research Center in the Erik Jonsson School of Engineering and Computer Science, University of Texas at Dallas.
Abstract :
Data streams are continuous flows of data. Examples of data streams include network traffic, sensor data; call center records and so on. Their sheer volume and speed pose a great challenge for the data mining community to mine them. Data streams demonstrate several unique properties: infinite length, concept-drift, concept evolution and limited labeled data. Concept-drift occurs in data streams when the underlying concept of data changes over time. Concept-evolution occurs when new classes evolve in streams. Data streams may also suffer from scarcity of labeled data since it is not possible to manually label all the data points in the stream. This tutorial will present an organized picture on how to handle various data mining techniques: in particular, how to handle classification problem in stream domain, and how to handle clustering in evolving streams.
During this tutorial we also present how the aforementioned properties are addressed for handling the data mining techniques.
Tutorial Outline:
We will introduce stream mining with examples, and present its characteristics and challenges and current state of the art, and its application to security.
- Introduction,
- Data mining applications for security,
- Suspicious event detection,
- Face detection
- Web page prediction
- Building a classification model using scarcely labeled training data based on semi-supervised clustering and active learning.
- Techniques that address all four major challenges to data stream classification: infinite length, concept-drift, concept-evolution, and limited labeled data.
- Classification techniques for evolving data streams (i.e., feature set changing along with concept evolution) focusing on textual stream.
- Clustering techniques for evolving data stream.
- Applications of stream mining in various domains including
- Current state of the art of data intensive stream mining using cloud computing, namely, Hadoop.
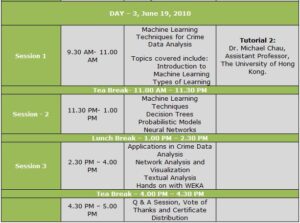
Tutorial 2: Machine Learning Techniques for Crime Data Analysis by Dr. Michael Chau, Assistant Professor, The University of Hong Kong.
- Introduction to Machine Learning
- Types of Learning
- Machine Learning Techniques
- Decision Trees
- Probabilistic Models
- Neural Networks
- Applications in Crime Data Analysis
- Network Analysis and Visualization
- Textual Analysis
- Hands on with WEKA
Faculty:
- Dr. R.N.Prasad, Senior Lead Principal, Education & Research — Infosys Technologies Ltd., Mysore & his Team.
- Dr. Bhavani Thuraisingham, Professor of Computer Science and Director of the Cyber Security Research Center in the Erik Jonsson School of Engineering and Computer Science, University of Texas at Dallas.
- Dr. Michael Chau ,Assistant Professor,The University of Hong Kong.
URL: http://www.business.hku.hk/~mchau/
Workshop Chair:
Shalini R. Urs
Executive Director and Professor
International School of Information Management, University of Mysore
URL: http://www.isim.ac.in/shalinirurs.htm
Registration Details:
| Registration Fee (Corporate) | : INR 4000 |
| Registration Fee (Academic) | : INR 2000 |
| Registration Fee (Students) | : INR 1000 |
(Accommodation available on twin sharing basis costing Rs. 1,000/- per day)
Payment Mode Details:
Payment can be made through either DD or Wire Transfer.
Contact for registration:
Lohith Krishnamurthy
- Mob: +91 9886772356
- Email: lohith@isim.ac.in
